BaseCTF 2024 Week1 Writeup
BaseCTF 2024 第一周赛题的 WP,热身赛捏。
在小羽网安的公众号看到的,本来毕设已经很焦虑了,但是就是主打一个主次不分。
Misc
根本进不去啊!
1 | |
海上遇到了鲨鱼
复制文本然后执行以下 Python 脚本
1 | |
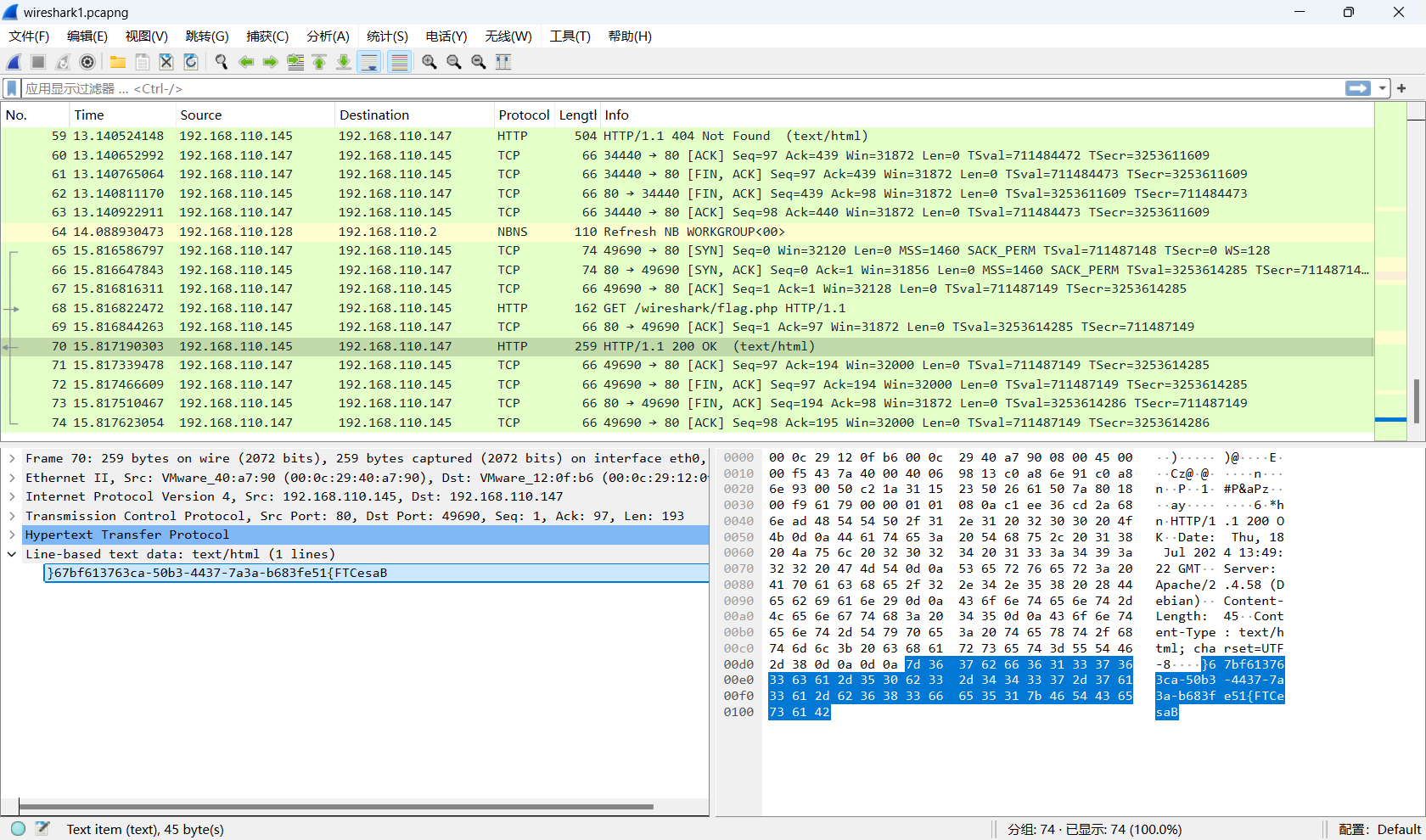
正着看还是反着看呢?
看到最后是一个 JFIF 的倒着写,执行下面的 Python 脚本将文件倒过来
1 | |
binwalk 查一下文件,发现 flag.txt
和一个压缩包,以为是个假的,压缩包解压出来也是,那就交了吧。
Base
后面6个等于号,大概是 Base 编码系列但是不是 Base64。分析一下编码结果,发现只有大写字母和一些数字,那么大概率是 Base32 了,解一下发现好像是 Base64,再解一下就flag了。
人生苦短,我用Python
1 | |
Crypto
ez_math
看来不是标准解,两个三角矩阵6个未知量加上 \(a, b, c, d\) 与 flag
5个共11个未知量,矩阵是9个等式,2个乘积2个等式,可以解出
flag。用 sagemath 解。
1 | |
babypack
output.txt 太大了,直接改名为
output.py,原理尚不清楚,但是大概是因为每个比特的数字都大于低位比特数字之和,所以应该是不存在选择当前位与选择一些低位之和冲突。
1 | |
babyrsa
1 | |
十七倍
17 = 0b10001,高4位减去低4位得到原始的高4位,注意也许要退位。
1 | |
helloCrypto
1 | |
ez_rsa
\(\varphi(n) = (p-1)(q-1) = n - (p+q) + 1\),\(\varphi' = (p+2)(q+2) = n+2(p+q) + 4\),用 \(\varphi'\) 求出 \(p+q\) 即可求出 \(\varphi(n)\)。
1 | |
你会算md5吗
1 | |
Pwn
最差的一部分,得好好补补了。这部分只做了两题,会用 nc 会用基础的 linux 命令即可,就不放在这里丢人现眼了。
Web
HTTP 是什么呀
正好练习一下 curl,最后所有都对了就是没输出,所以用
--verbose 参数看一下到底发生了什么。发现是重定向了,而且
flag 在 url 里面。
1 | |
喵喵喵´•ﻌ•`
1 | |
md5绕过欸
1 | |
A Dark Room
F12
upload
写如下的脚本并上传,然后访问
http://host:port/uploads/filename.php
1 | |
很好奇为什么不能使用
$_GET参数来执行system命令
Aura 酱的礼物
感谢 Vercel 的大力支持
花了好久,最后歪门邪道搞出来了。
首先是读 $_POST['pen'] 的文件,那么直接伪协议
data://text/plain;base64,QXVyYQ== 绕过。
接着是要求 $_POST['challenge'] 以
http://jasmineaura.github.io
开头,并且从该变量获得的内容中包含指定内容,做题的时候大概有以下2点思路:
- 看看这个网站上有什么可以内容注入的点,比如说一般的博客在内容搜索的时候,加入内容不存在,会说 “未找到 xxx”,那不就包含了。(不知道静态网页能不能做,反正是审计的内容)
- 找
strpos和get_file_contents函数的漏洞绕过。
发现没什么用,有 search.js
文件但是没用,strpos 和 get_file_contents
也是弱类型绕过,这里好像没用。
忽然灵光一闪,我可以用
http://jasmineaura.github.io.bcb.pub
解析到一个服务器上,返回指定内容就好啦。因为没有备案的服务器,所以 A
解析在国内没用。正好前面搞了 CNAME
解析,看看能不能搞一个服务器,或者只要静态网页托管就行了。
服务器这方面,Vultr 至少需要充 10 USD;Google Cloud 没有信用卡不然可以白嫖。静态托管这方面,Github Page 的话不想搞乱博客(其实在 Github 上也看到了一些为了解这题创建的项目,试图 CNAME 蹭蹭但是失败),GitLab/Gitee 也都有部署/审核的麻烦。最后选择了 Vercel 的服务,可以支持 CNAME。设置一下绕过判断。
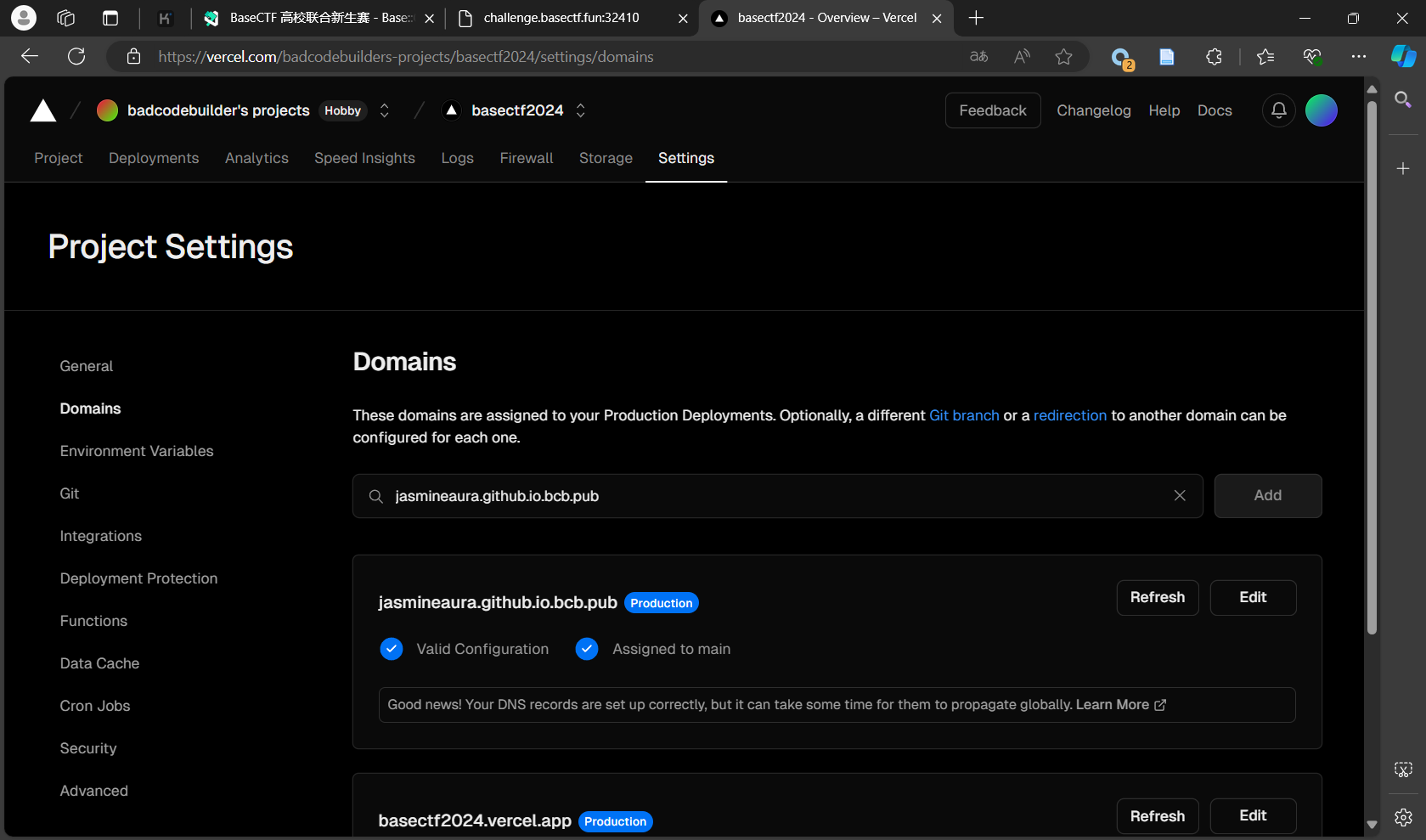
最后就是一个
php://filter/read=convert.base64-encode/resource=flag.php
带出信息。
Reverse
感谢 52pojie 的资源
You are good at IDA
1 | |
1 | |
UPX mini
直接运行?忘了
Ez Xor
一开始没怎么看懂密钥是怎么生成的,动态调试了一下直接拿到密钥,再与数据对比分析一下才看懂,其实是数据的大小端问题。0x726F58i32
从小端开始那么是
[0x58, 0x6F, 0x72, 0x00],但是从大端开始就说不通了。想通这一点下面就都解决了。
1 | |
ez_maze
走迷宫那么必然有迷宫,Shift+F12 看到一堆 $ 和
&。数一下是225个,猜想15*15的迷宫,手动换行。看起来
& 像是路,手动替换。走路并手动走路。
验证一下:
1 | |
BasePlus
其实也是没有完全看懂代码,但是看到了编码的其中一段
1 | |
因为前段时间无聊,手写了一次 Base64编码,对这段位运算有点眼熟,然后看看 Secret,好像是自定义 Base64 编码集合。CyberChef 试一下发现居然是有名有姓的,叫什么Atom128。但是解码不对,看起来与原始信息差了一些,继续看代码发现还有异或,再试一下就解出来了。
1 | |
结尾
补题!做毕设!